REGISTRY AND MALWARE PERSISTENCE
This amazingly interesting post describes persistence techniques malwares use today via Registry entries.
Malwares have been an interesting topic of research since the very first computer virus was developed called a "Brain". Malware development has tremendously evolved since then. Our team observes new strains of virus samples everyday. One of the interesting topics of the malwares is their persistence techniques. Persistence is the ability of malware to start itself everytime a computer is turned on.
WHAT IS REGISTRY
The database where all the settings of the Windows are stored is called a registry. It is arranged in a hierarchical order to retrieve data whenever needed and used in the system.
The below provided registry keys are what malwares uses to achieve persistence state.
BOOT EXECUTE KEY
A processor in a computer running Windows has two different modes: user mode and kernel mode. The processor switches between the two modes depending on what type of code is running on the processor. Applications run in user mode, and core operating system components run in kernel mode.
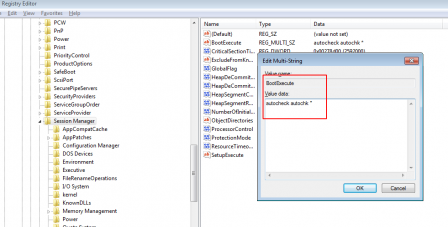
Session manager (smss.exe) is the first user mode process that is launched . One of the entries where malwares persist is the BootExecute key. This key lies at:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager
If the entry shows anything apart from the default values of autocheck autochk * as shown in below image this could be an indication of possible malware.
SERVICE KEYS
Winload.exe (Windows Boot Loader) is a small piece of software, called a system loader, that's started by BOOTMGR, the boot manager used in Windows 10, Windows 8, Windows 7, and Windows Vista operating systems. Its job is to load essential device drivers, as well as ntoskrnl.exe, which is a core part of Windows.
The winload.exe loads the device driver during startup. These drivers are configure in below path
HKLM\system\currentcontrolset\services
During assessment the ImagePath entries are checked for any executables.
The Start key:value denotes
- 0 Kernel drivers (load before kernel initialization)
- 2 Autostart
- 3 Manual start via Service Control Manager (SCM)

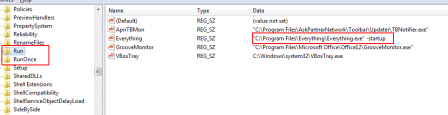
RUN SERVICE KEYS
These keys allows a program to run each time a user logs on. You can write multiple entries under a key. If more than one program is registered under any particular key, the order in which those programs run is indeterminate.
The Windows registry includes the following four Run and RunOnce keys:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
WINLOGON KEYS
This proces is started by wininit.exe which handles logon and logoff. The process "winlogon.exe" runs in the background. Winlogon is a part of the Windows Login subsystem, and is necessary for user authorization and Windows activation checks. Following four registry keys are related to winlogon process
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell
- Notify: Programs to run upon events like logon, logoff, startup, shutdown, startscreensaver, and stopscreensaver
- Userinit: Programs to run when a user logs in
- Shell: Programs to run when Userinit will launch. Default shell is Explorer

The entry in Userinit has been modified to show how a malware persists by modifying these entries.
Shell Service Object Delayed Load (SSODL)
This entry Instead of pointing to the file itself, it points to the CLSID's InProcServer, which contains the information about the particular DLL file that is being used. The registry path can be observed under
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad
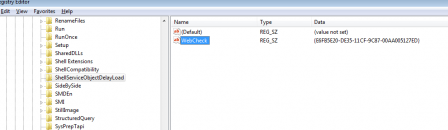
The entries under this key is loaded automatially by windows explorer.
E.G. Trojan/Muddle creates a random entry under ShellServiceObjectDelayLoad and registers its DLL as a COM object under HKCR\CLSID\
RUN KEYS (RUN, RUNONCE, RUNONCEX)
These keys are most abused and a common way to make startup entry. A malicious user can make entries under below keys to achieve persistence. Majority of the applciation installed use the same set of registry keys to achieve startup.
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnceEx HKLM\Software\Microsoft\Windows\CurrentVersion\Run HKCU\Software\Microsoft\Windows\CurrentVersion\Run HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run

LOAD KEYS
Less commonly used, if found these keys can also achieve persistence. Cardinal RAT is such an example which uses these load keys to achieve startup.
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\load HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows
APPINIT DLL
The AppInit_DLLs registry value contains a list of dlls that will be loaded when user32.dll is loaded. Malicious AppInit DLLs may also provide persistence by continuously being triggered by API activity. The AppInit DLL functionality is disabled in Windows 8 and later versions when secure boot is enabled. Some variants of CherryPicker use AppInit_DLLs to achieve persistence by creating the following Registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows "AppInit_DLLs"="pserver32.dll"[

Comments off